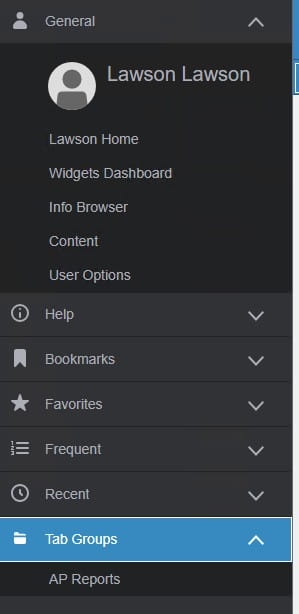
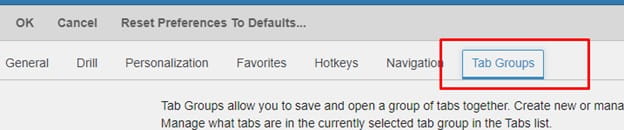
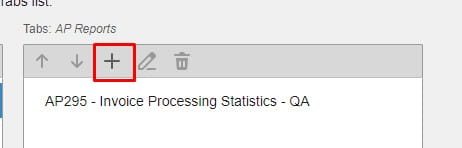
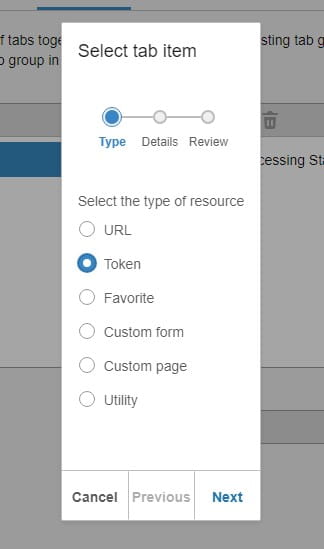
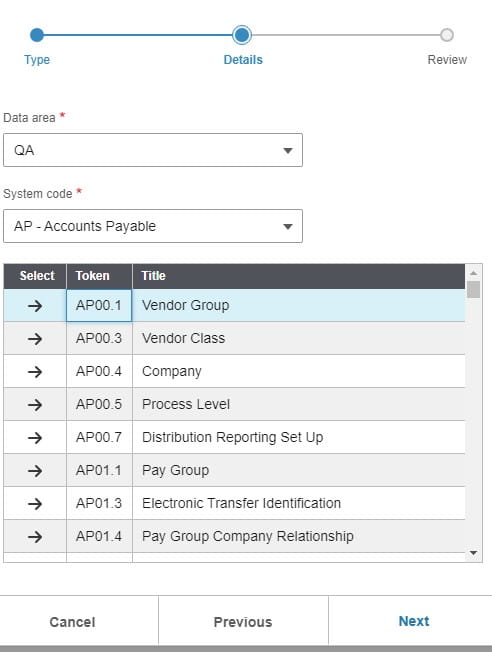
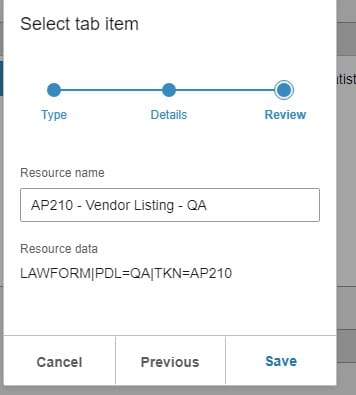
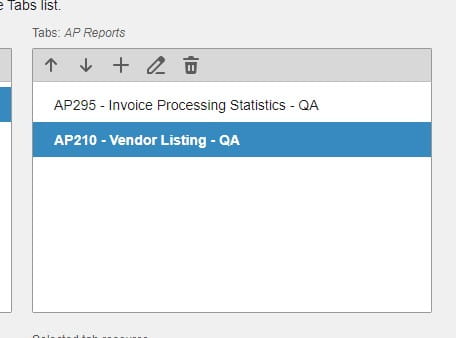
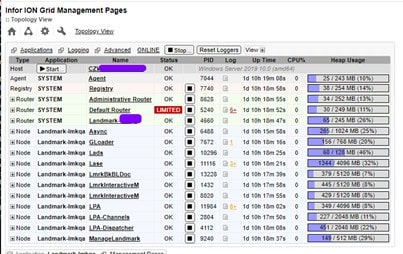
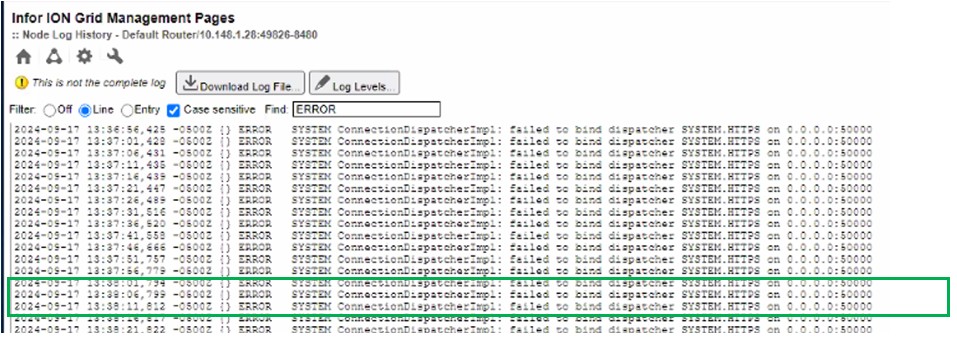
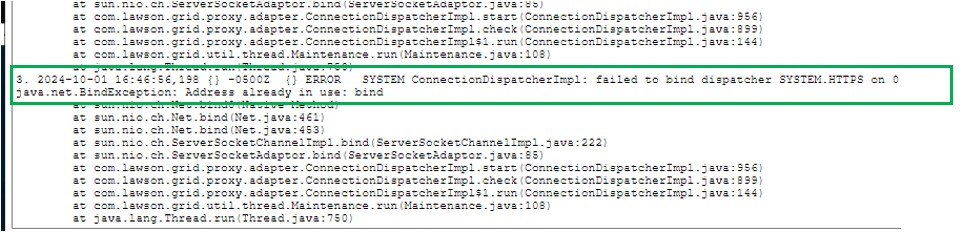
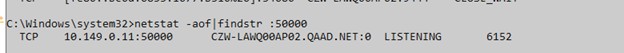
Cloud-based enterprise resource planning (ERP) has transformed the way businesses implement, manage, and scale their systems, providing flexibility, real-time updates, and ongoing enhancements. However, as more industries adopt Cloud ERP, many companies face challenges in fully unlocking the value of their investment. Infor’s Senior Solution Marketing Manager Doug Heise, shares an informative blog about discussing the evolving role of ERP support in the cloud era. As businesses increasingly move their enterprise resource planning (ERP) systems to the cloud, the traditional support models are becoming outdated. The blog emphasizes the need for a customer-centric approach that integrates modern technologies and practices. Heise highlights the benefits of cloud-based systems, including scalability, flexibility, and improved access to data. The post argues that cloud ERP support must adapt to these new environments, offering real-time assistance and proactive solutions. He also points out the importance of collaboration between vendors and clients to address specific business needs effectively. Additionally, should not only focus on problem resolution but also on enhancing the overall user experience. It advocates for harnessing AI and machine learning to provide smarter, more efficient support solutions. Furthermore, it stresses the significance of continuous training and education for users to maximize the value of their ERP systems. Heise concludes by stating that redefining ERP support in the cloud era is crucial for businesses looking to stay competitive and agile. Embracing these changes can lead to improved operational efficiencies and a stronger partnership between organizations and their ERP providers.