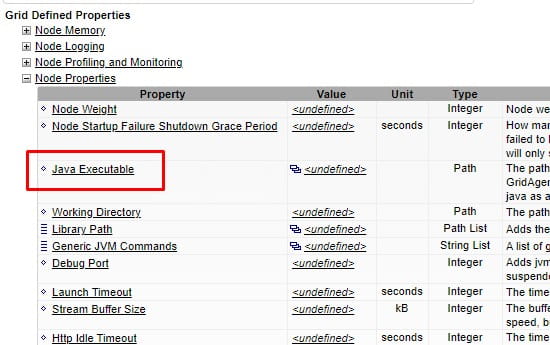
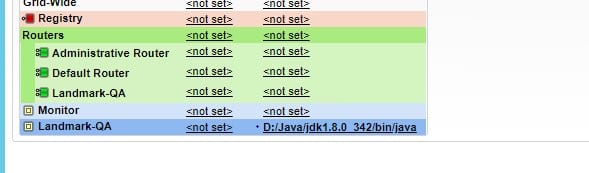
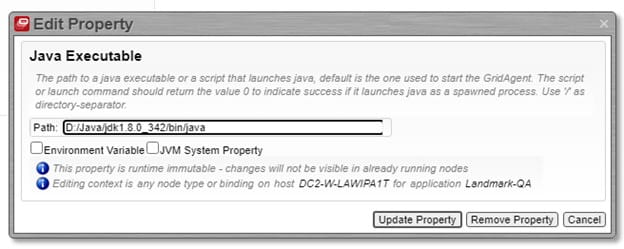
To debug batch programs through command-line entry, use the following steps:
To debug batch programs through command-line entry
- If LAWENV is not called as part of your user profile’s sign-on program, you must call the LAWENV program to set the environment variables correctly.
- At the IBM i command line, type
CALL LAWENV - Type the name of an Environment and press Enter.
- At the IBM i command line, type
- Compile the program you want to debug. At the Qshell command line, type
qcompile -D productline systemcode programcode
Note: If you need to include modules in the compile, use qcompile -Dm productline systemcode programcode .
- Submit the program to a job queue that is on hold or is not tied to a subsystem (so that the batch job does not execute).
- Start a service job for the program.
- Get the job information by typing at the IBM i command line,
WRKJOBQ QueueName
where QueueName is the job queue to which you submitted the batch program.Select option 5 (Work with) for the job queue and then write down the job, user, and job number information for the appropriate job.Note: You can also use the WRKUSRJOB command to find the job information, but this may yield a much longer list of jobs to view in order to find the one you need. - At the IBM i command line, type:
STRSRVJOB JobNumber/UserName/JobName
- Get the job information by typing at the IBM i command line,
- Start debug. At the command line, type STRDBGand prompt it (F4). Make sure the library is the one where you compiled the source and that UPDPROD(*YES) is set. If the information is correct, press Enter.
- When source listing appears, press F12to resume.
- Start the batch program by changing the job to run in an active queue. On the “Work with Job Queue” screen, enter 2(Change) to change the job queue for the job. After typing in the job queue name, press Enter.The ILE debugger will display the “Start Serviced Job” screen with the following message: “The serviced job has been released from the job queue. Press Enter to start the job or F10 to enter debug commands for that job.”
- Press F10and then at the IBM i command line, type:DSPMODSRC
- Set break points (F6), then press F12, and then press F3 to return to the “Start Serviced Job” screen.
- Press Enterto run the program.
- After finished with debugging, end debug and the service job. At the IBM i command line, type:
ENDDBG
thenENDSRVJOB