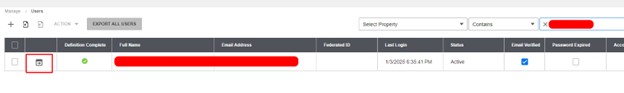
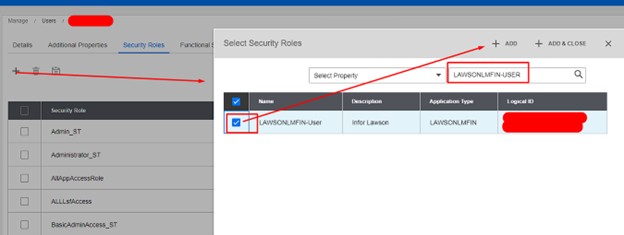
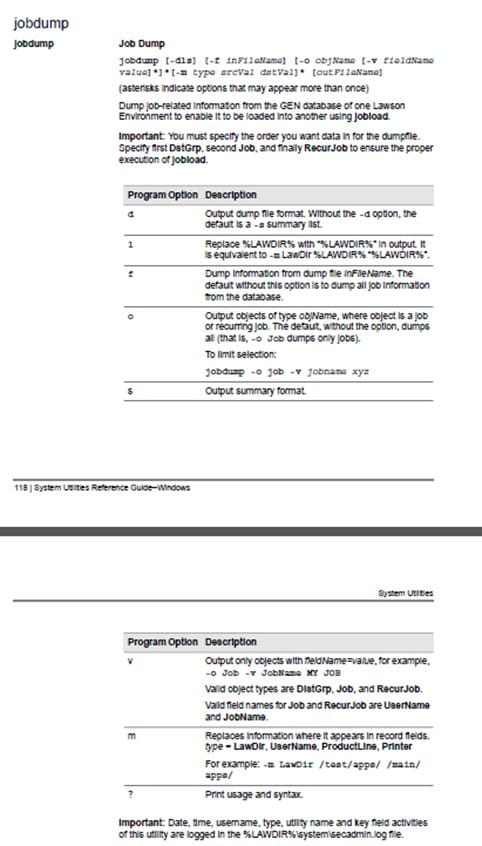
Traditional enterprise resource planning (ERP) systems are becoming digital dead weight. In a recent article by ERP Today’s CEO Mark Vigoroso, he explains why more organizations are ditching monolithic platforms in favor of composable ERP—modular, flexible systems built for change. Historically, companies showcased large, customized ERP implementations that were rigid and difficult to adapt. However, market data indicates a strong move toward composable ERP solutions, with 76% of IT decision-makers aware of them and 84% planning investments, reflecting a rapid industry transition. Traditional ERP platforms, designed for slower-paced business environments, often require extensive customization, leading to costly and time-consuming upgrades. In contrast, composable ERP leverages APIs and microservices, enabling businesses to quickly add, swap, or modify modules without disrupting the entire system. This approach aligns with the modern need for agility in fast-changing markets. Nextworld exemplifies this shift by separating applications from underlying technology, allowing seamless updates and future-proofing. Its enterprise no-code platform empowers business users to develop and modify applications independently, reducing reliance on IT and avoiding technical debt. The company advocates for the “Clean ERP Method,” which modernizes systems without complete replacements, supporting integration and evolution. The article emphasizes that organizations sticking to legacy, monolithic ERP are becoming increasingly obsolete. Future-ready companies will adopt composable platforms that facilitate rapid application assembly, decompose and recompose solutions as needed, and create ecosystems of specialized tools. For ERP leaders, this means shifting focus from static functionalities to adaptable, integrated ecosystems—prioritizing platform thinking, reducing technical debt, and enabling seamless integration of best-of-breed solutions through open standards.
For Full Article, Click Here