We had trouble with the Infor Lawson Query Wizard either timing out or returning a “No Data Found” message when loading in a .dme query.
This is a compiled list of troubleshooting suggestions for the Query Wizard found on Nogalis presentations/Infor documentation/Lawsonguru forums.
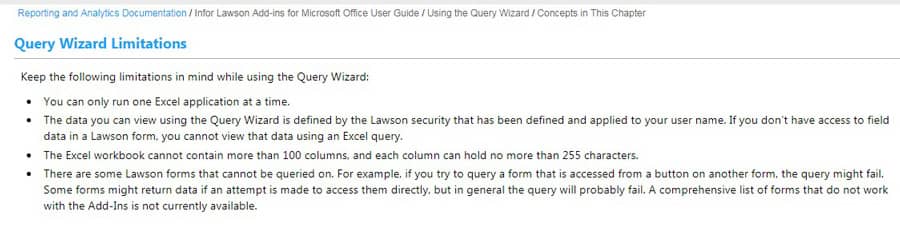
1. Limitations of the Query Wizard
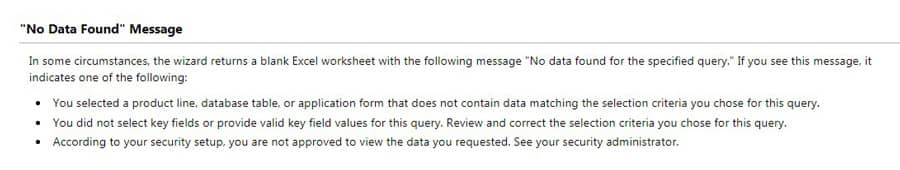
- “No Data Found” Message
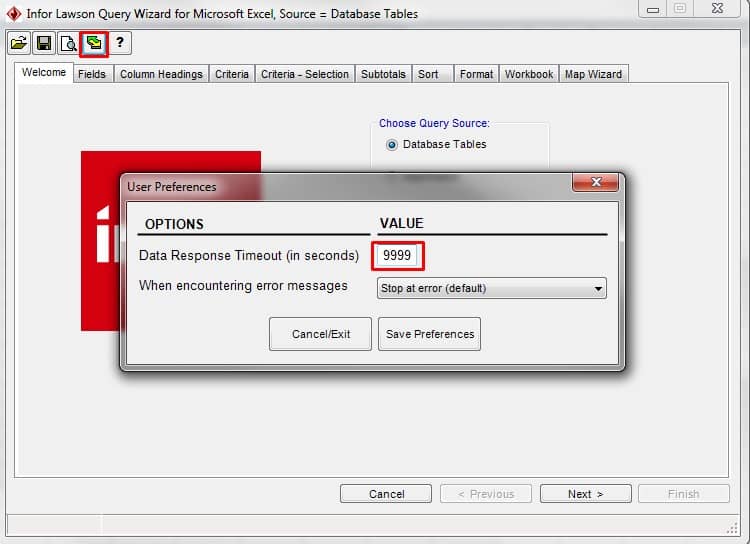
- Try increasing Data Response Timeout value to 9999 (min 30 max 9999) in Set User Preferences (green/yellow arrows)
If this fails, try experimenting with the different options for When encountering error messages
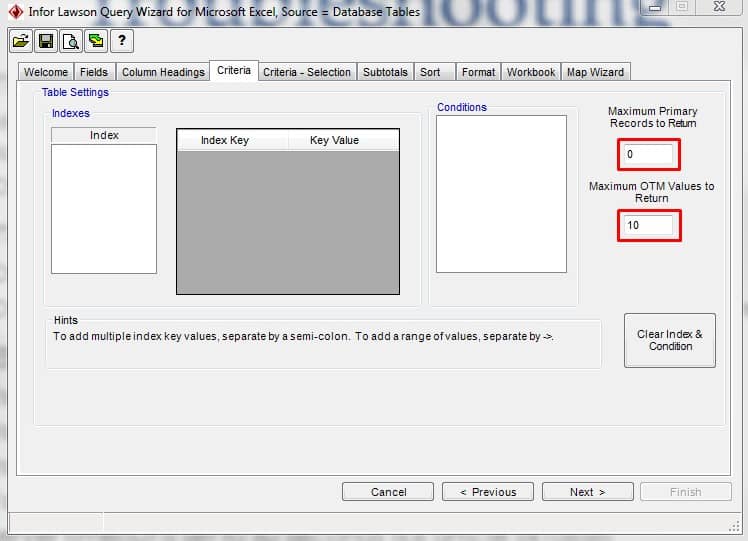
- On the Criteria tab, try changing Maximum Primary Records to Return to 0 (default 600, max 65520, 0 defaults to max 65520) and Maximum OTM Values to Return (max 600) fields
- Troubleshooting tips from Nogalis LawsonMSAddins PowerPoint