If you are testing your MSCM handheld connection against the secured MSCM URL, and getting a “Test Failed” error, you may need to modify the Quality of Protection protocol in WebSphere.
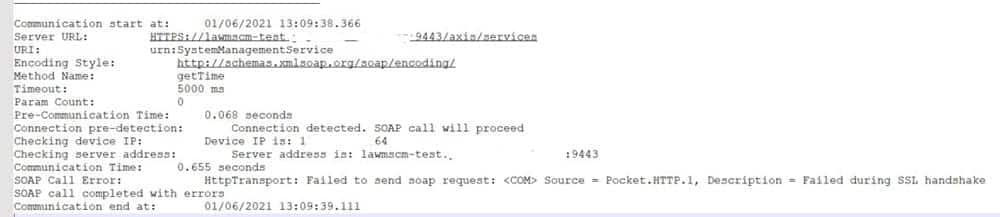
The symptoms of the issue are: “Test Failed” message on the handheld, and the MSCM COMM log will show an error stating “Failed during SSL handshake”.
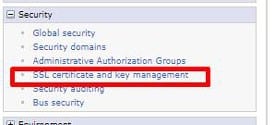
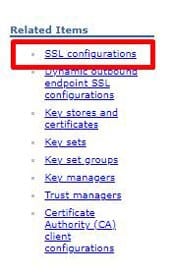
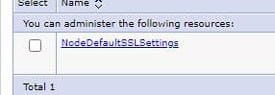
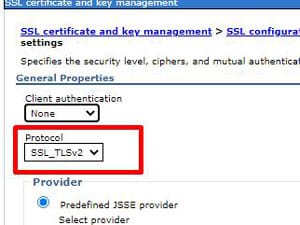
To update the QoP protocol in WebSphere, open the WebSphere Admin Console for MSCM, and navigate to Security > SSL certificate and key management. Click “SSL configurations” on the right side of the page. Then select the NodeDefaultSSLSettings. Click “Quality of protection (QoP) settings” on the right. Update the Protocol to “SSL_TLSv2”. Click “Apply” and save the configuration. Repeat these steps for the cell (if applicable), then restart WebSphere services for MSCM.
**NOTE: To avoid future issues with the MSCM/Lawson connection, it is best to set the QoP protocol in the LSF WebSphere Console to the same values as MSCM. Do this both for the Node and the Cell.
Infor recently updated handhelds and MSCM for a cloud environment. The test user was able to download the Infor CAB files to the handheld but was unable to download the PlatformDLL file. The error message kept coming back with “Internet Explorer cannot download file”
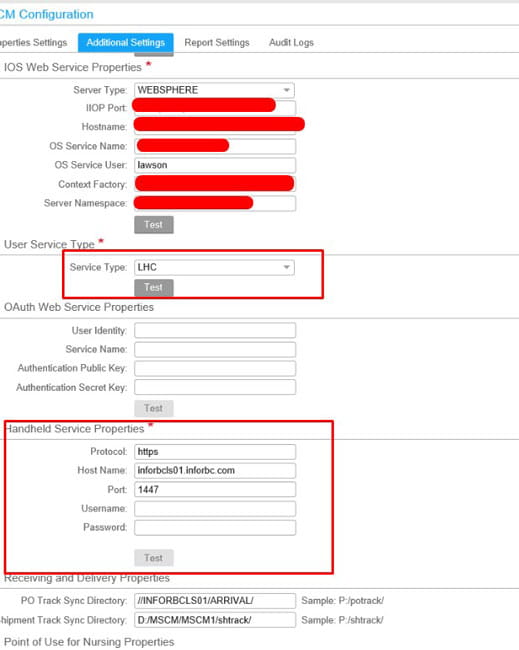
After ensuring all permissions were set for the user and running several tests, rechecking the configuration setup. We finally located the issue from the update and it turns out a port was reset to a default value and we had to change the Service Type to LHC. Below are the steps you can take to resolve this if you’re experiencing a similar issue.
- Login into MSCM with Server Administration group rights.
- Select MSCM Configuration >> Additional Settings
- Select Service Type LHC and under Handheld Service Properties, ensure you’re using the correct port. For us we had to update it to 1447
- We updated both LSF and handheld ports to 1447 and the user was now able to download the file.
Hope this was helpful!
If you have suddenly noticed in Lawson Security Administrator that certain users have different attributes in their addins field other than ALLOW or DENY, don’t worry as this was setup by design back before LSF version 9.
These values were removed in version 9+ because Lawson User Security (LAUA) and Lawson System (LS) security can now secure these actions on specific tables and records.
If you want to convert the old Addins Attributes like to Allow or Deny, simply edit the users RM info and change the Addins field to Allow or Deny.
If you prefer to stay on the older attributes, see the table below for in-depth access descriptions:
| Attribute ID | Description |
| Dxxxx | The user does not have access to the Query Wizard, but has full access to the Upload Wizard. |
| DDxxx | The user does not have access to any Addins functionality. Same as the current Addins attribute = DENY. |
| ADxxx | The user has access to full QueryWizard functionality, but is blocked from using any part of the UploadWizard. |
| AADDD | The user has access to both the QueryWizard and the UploadWizard, but is blocked from adding, changing, and deleting records. |
| AAADD | The user can use the QueryWizard and UploadWizard to add records only. |
| AADAD | The user can use the QueryWizard and the UploadWizard to change records only. |
| AAAAD | The user can use the QueryWizard and the UploadWizard to both add and change records, but is blocked from deleting records. |
| AADDA | The user can use the QueryWizard and the UploadWizard todelete records only, but is blocked from adding or changing any records. |
| AAADA | The user can use the QueryWizard and the UploadWizard to add and delete records, but is blocked from changing any records. |
You’ve applied a patch to your system and it caused more problems than it fixed or it was not the solution to your problem and there is no point in pushing it to PROD. Today we are going over simple steps to uninstall a CTP which is similar to how you install a patch via lawappinstall.
- Ensure security is turned off and it is typical to bring down websphere before starting so no user can login during this process.
- In LID, start with the uninstall command:
- perl %GENDIR%\bin\lawappinstall uninstall <productline> <patchxxxxx>
- Run lawappinstall STAGE (optional but recommended)
- perl %GENDIR%\bin\lawappinstall stage <productline>
- Verify stage compilation complete:
- qstatus | wc -l (this command will return the number 4 when compiling is complete)
- Check for compiling errors:
- ls %LAWDIR%\<productline>\*\*.err
- If any errors found, recompile failed programs with this command:
- qcompile productline SystemCode ProgramCode
- If any errors found, recompile failed programs with this command:
- ls %LAWDIR%\<productline>\*\*.err
- Run lawappinstall VALIDATE:
- perl %GENDIR%\bin\lawappinstall validate <productline>
- Run stgcmp
- stgcmp list <productline>
- If the program’s status is FAILED or RECOMPILE REQUIRED, submit the program to the compile queue using the -A option.
- stgcmp list <productline>
- Finally, Activate
- perl %GENDIR%\bin\lawappinstall activate <productline>
- You should see the patch(es) you ran the initial uninstall for, confirm, verify any other prompts.
- perl %GENDIR%\bin\lawappinstall activate <productline>
- Verify Non-stage compilation (if you didn’t run stage):
- qstatus | wc -l
- Turn security on, turn websphere on, run your typical post smoke tests as if you were applying a patch.
Hope this was helpful!
IOS debug logging can be useful for tracking down issues in Lawson Portal, Add-ins, and Ming.le. There are two methods to enable it, we prefer method 1 below.
Method 1 (ios_logging.properties file must be renamed or deleted for this method to work):
- Login to your LSF on-prem server (Admin access required)
- Make a backup copy of your xml in %LAWDIR%\system
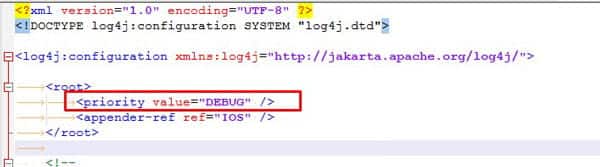
- Edit the xml file with a text editor.
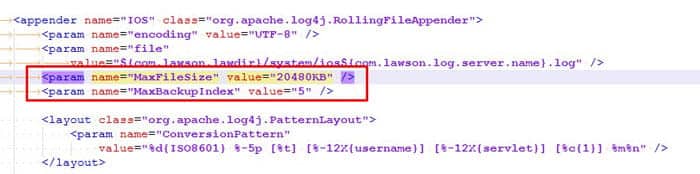
- Change INFO to DEBUG as shown below
- If using DEBUG (or prefer a longer history of logging), you also may want to increase the log file size MaxFileSize and maximum number of logs to be generated MaxBackupIndex
Below our IOS logs will be 20mb and we will have a max backup of 5.
You should now see DEBUG entries in the log.
Method 2 – ios_logging.properties (this will be used by default over ios_logging.xml if it exists)
- As the lawson user, make a backup copy of ios_logging.properties in %LAWDIR%\system (if it exists).
- Copy the ios_logging.properties file from %GENDIR%\install to %LAWDIR%\system (you will only need to do this once to update the formatting of the ios_logging.properties file with the latest delivered version from %GENDIR%\install).
- Edit the ios_logging.properties file in %LAWDIR%\system:
- Change the second line in the file from INFO to DEBUG.
##Set root logger level to DEBUG and its only appender to A1.
log4j.rootLogger=INFO, IOS
to:
log4j.rootLogger=DEBUG, IOS
- Change these lines:
log4j.appender.IOS.MaxFileSize=2048KB
log4j.appender.IOS.MaxBackupIndex=5
to:
log4j.appender.IOS.MaxFileSize=20480KB
log4j.appender.IOS.MaxBackupIndex=5
This increases your log from 2mb to 20mb with a max of 5 log files. Adjust based on how busy your system is.
NOTE: A restart of WebSphere is not needed for these changes unless you are switching between ios_logging.properties and ios_logging.xml.
You should now see DEBUG entries in the log.
Good luck and happy debugging!
Sometimes after applying a patch, drill-around and drop-down boxes don’t get properly rendered on certain forms. Below are some steps to check which forms may have been affected and how to resolve them.
- Assuming you’re logged into LID, change directories to your %LAWDIR%\<productline> directory
- Run this command: attrib /s *err
- You may see common errors such as: %LAWDIR%\<productline>\XXsrc\PROGRAM.err
- These can be resolved via running qcompile and then clearing IOS cache (also your browser cache, logging out and back in).
- However, a less common error %LAWDIR%\<productline>\XXsrc\PROGRAM.scr.xmlerr cannot be resolved by simple recompiling.
- This error typically has to do with forms that have drill-around and drop-down boxes.
- You may see common errors such as: %LAWDIR%\<productline>\XXsrc\PROGRAM.err
- To resolve PROGRAM.scr.xmlerr errors, we must run srgen and then scrgen
- If lawappinstall stage failed to run scrgen and hasn’t been activated you can run the following commands in the below order:
-
- srgen -A <productline>
- scrgen -A <productline> <systemcode> <program> (for the programs with the .scr.xmlerr files in XXsrc directories).
-
- If you’re spotting the .scr.xmlerr files after activating a patch successfully, run the following commands in this order:
-
- srgen <productline>
- scrgen <productline>
- Check to see if the .scr.xmlerr still exist.
- Run qcompile for each program with the .xmlerr manually or run a cobcmp <productline> to compile the entire productline.
- Run: qcontrol -jlocal,8 (this will increase amount of compile jobs from 2 to 8, change back to 2 after)
- Run: qstatus | wc -l (this will show you how many compile jobs are remaining, when it hits 4, compiling is done).
-
- If problem persistes, repeat step 5, make sure you’re clearing IOS, server, and browser cache, logging out and back in. Give some time in between testing.
Good luck and happy debugging!