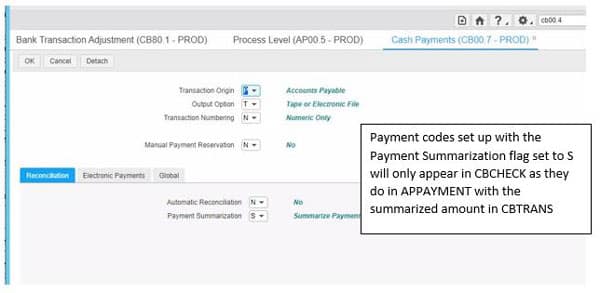
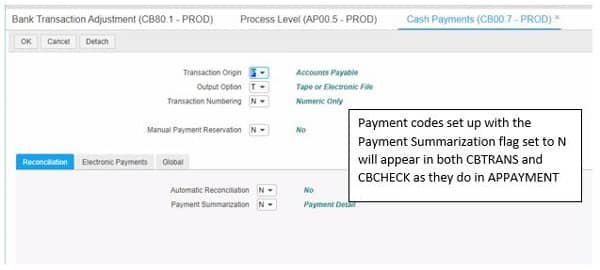
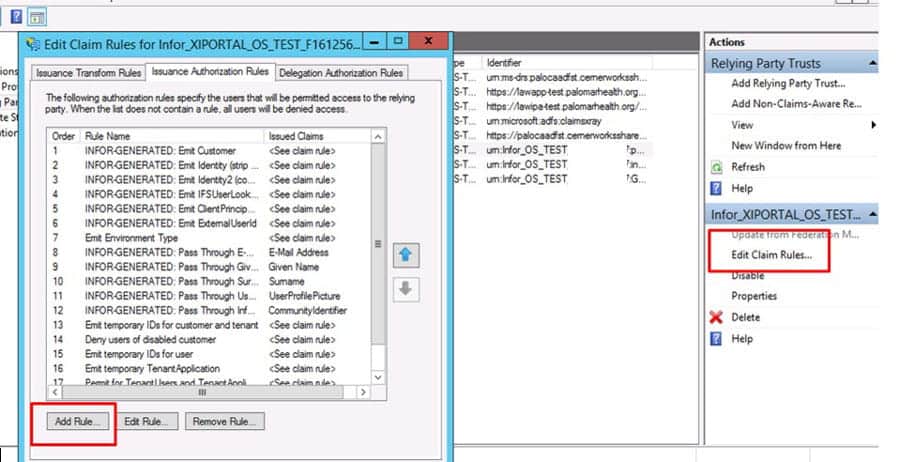
You want to work with an IT partner that has functional knowledge in addition to the technological ability to extract and re-map the data. This allows a true partnership that looks at the process from a high level and keeps an eye on the details at the same time.
You need to look for a partner that has experience extracting data from Lawson and mapping to the format needed to upload set up and transactional data to any system and taking extracted data from another system and formatting it into what Lawson needs and uploading the data. A partner who uses a repeatable process that allows for tweaking the process if needed through testing cycles and then having the final version ready when you are ready to go-live.
When considering a Merger or acquisition there are many considerations. Some of these are:
- Will there be a one-time conversion and at the end everyone will be using the same system?
- Or will there be an on-going interface between the systems for GL data only or other systems as well?
- Do you need a full training plan?
- How will the users be trained on the new system or processes?
- Make sure to start with a BRD – Business Requirement Document – so you have a road map of what is expected throughout the process. This helps both you and your partner know what is expected from both parties.
With the right partner, you can have a smooth and successful transition.