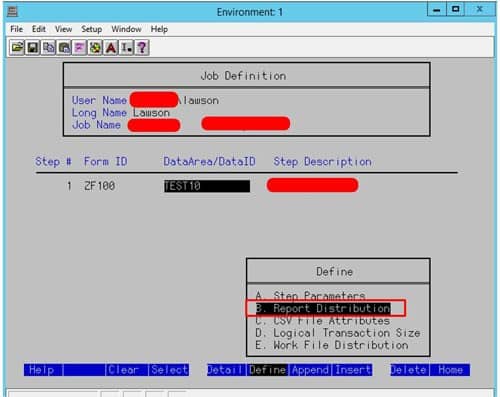
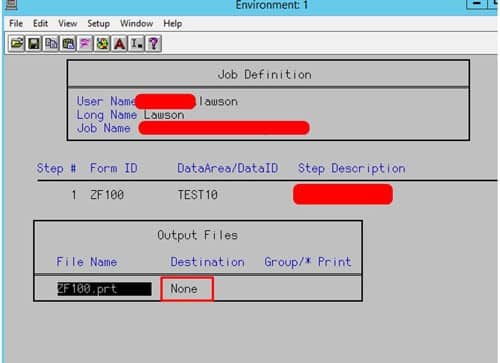
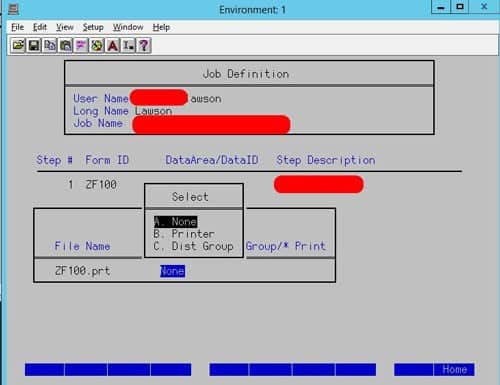
A user accesses their inbasket they can see the workunit and the associated data, however when they approve the requisition it leaves their inbasket view in portal with a success message. The workunit does not move on, nor does it show action has been taken within the workunit.
Also, no actions can be taken from that workunit.
Error from the lps.log
Thu Jun 16 14:19:48 PDT 2016 – Message “com.lawson.bpm.errors.ErrorMessages.com.lawson.rdtech.framework.ProcessFlowException: Unknown security exception has occurred.
at com.lawson.bpm.eprocessserver.grid.ProcessFlowExecutor.getActorContext(ProcessFlowExecutor.java:651)
at com.lawson.bpm.eprocessserver.grid.ProcessFlowExecutor.getActorContext(ProcessFlowExecutor.java:617)
at com.lawson.bpm.eprocessserver.grid.ProcessFlowExecutor.processProcessFlowQueue(ProcessFlowExecutor.java:409)
at com.lawson.bpm.eprocessserver.grid.ProcessFlowExecutor._executeFlowPrivate(ProcessFlowExecutor.java:332)
at com.lawson.bpm.eprocessserver.grid.ProcessFlowExecutor._executeFlow(ProcessFlowExecutor.java:212)
at com.lawson.bpm.eprocessserver.grid.ProcessFlowExecutorProcessorImpl.sweepPrivate(ProcessFlowExecutorProcessorImpl.java:284)
at com.lawson.bpm.eprocessserver.grid.ProcessFlowExecutorProcessorImpl.processMessage(ProcessFlowExecutorProcessorImpl.java:81)
at com.lawson.bpm.eprocessserver.grid.ProcessFlowExecutorProcessorImpl.runPrivate(ProcessFlowExecutorProcessorImpl.java:186)
at com.lawson.bpm.eprocessserver.grid.ProcessFlowExecutorProcessorImpl.run(ProcessFlowExecutorProcessorImpl.java:150)
at java.lang.Thread.run(Thread.java:744)
Caused by: com.lawson.security.interfaces.GeneralLawsonSecurityException: Unknown security exception has occurred.
at com.lawson.interfaces.security.LawsonSecurityFactory.setRunAsUserOnDuplicateContext(LawsonSecurityFactory.java:1549)
at com.lawson.bpm.eprocessserver.grid.ProcessFlowExecutor.getActorContext(ProcessFlowExecutor.java:634)
… 9 more
Caused by: java.lang.reflect.InvocationTargetException
at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at sun.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:57)
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:606)
at com.lawson.interfaces.security.LawsonSecurityFactory.setRunAsUserOnDuplicateContext(LawsonSecurityFactory.java:1545)
… 10 more
Caused by: com.lawson.security.authen.SecurityAuthenException: com.lawson.security.authen.LawsonUserContextImpl.security.authen.actor_does_not_support_run_as
at com.lawson.security.authen.LawsonUserContextImpl.setRunAsUserOnContext(LawsonUserContextImpl.java:1497)
at com.lawson.security.authen.LawsonUserContextImpl.setRunAsUserOnContext(LawsonUserContextImpl.java:1460)
at com.lawson.security.authen.LawsonUserContextImpl.setRunAsUserOnContext(LawsonUserContextImpl.java:1451)
at com.lawson.security.authen.LawsonUserContextImpl.setRunAsUserOnDuplicateContext(LawsonUserContextImpl.java:1592)
at com.lawson.security.authen.DataCtxUserCtxWrapper.setRunAsUserOnDuplicateContext(DataCtxUserCtxWrapper.java:432)
… 15 more
” not found.
Resolution:
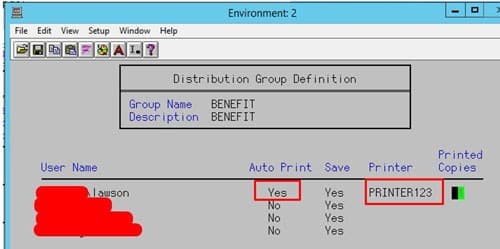
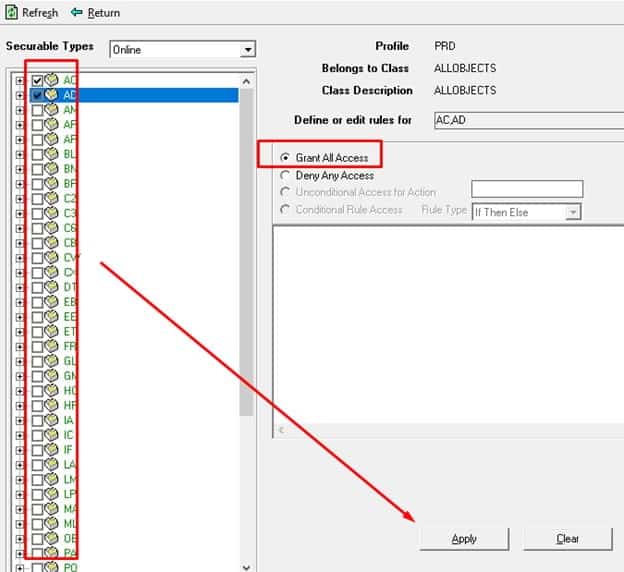
The lawson user does not have Run As enabled. Infor Security Administrator by default has the enable Run As set to “NO” for the lawson user. When a change is done on the lawson user and saved in the Infor Security Administrator the run as gets flipped back to “NO” in Landmark. Go to Infor Security Administrator and change the Enable Run As to “YES” save it. Restart LPA and Async grid nodes.
Keywords: