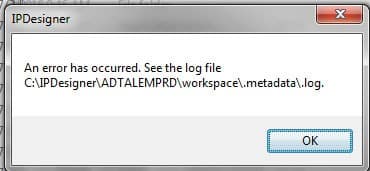
IIS Manager “Web Platform Installer” Troubleshooting
Nearly all guides regarding installing PHP in IIS recommend using the Web Platform Installer as it will take care of all the additional installs/configurations associated with PHP.
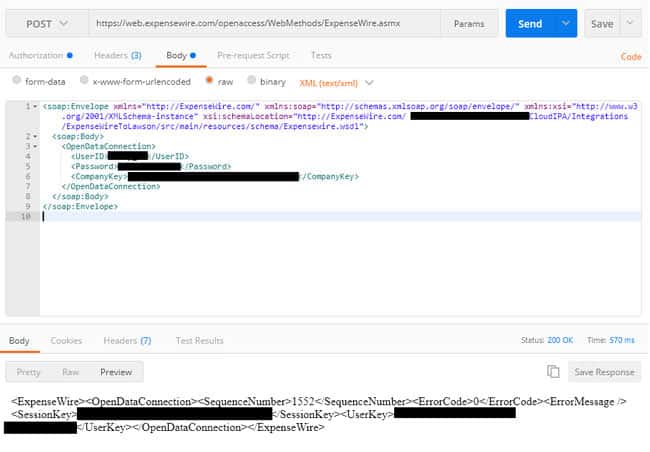
The Error:
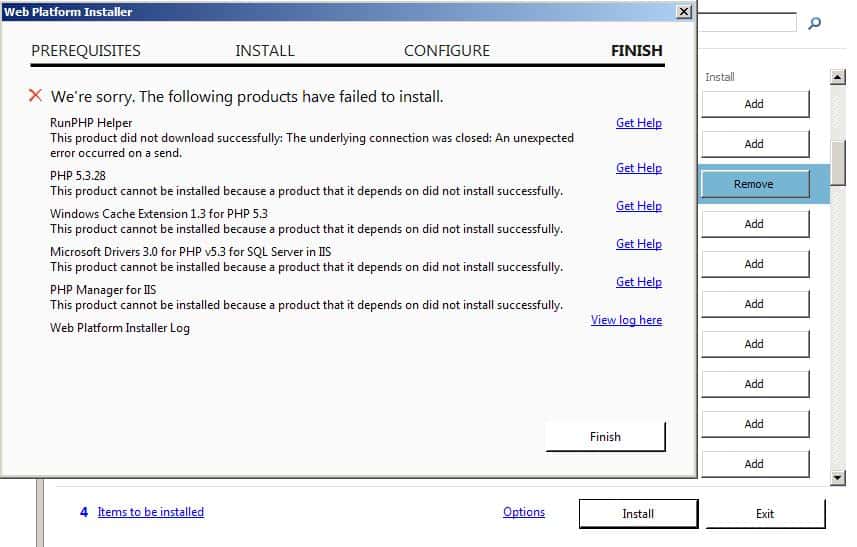
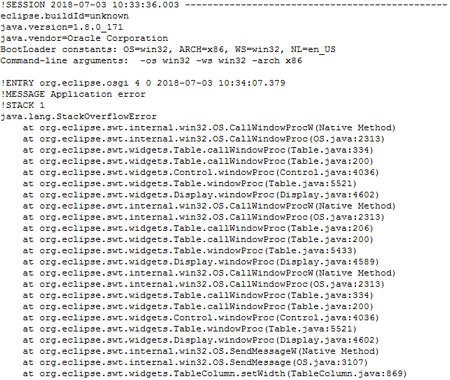
When attempting to install PHP through Web PI, this RunPHP Helper error occurs, which stops all of the following installs as well:
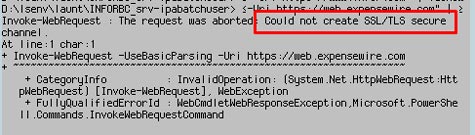
This occurs because IIS attempts to download RunPHP Helper from https://sourceforge.net/projects/phpinstallermsi/files/zip/runphp.zip/download using Internet Explorer (IE). Unfortunately, Internet Explorer has issues accessing that site even if it will work perfectly fine in Chrome or other browsers.
The Solution:
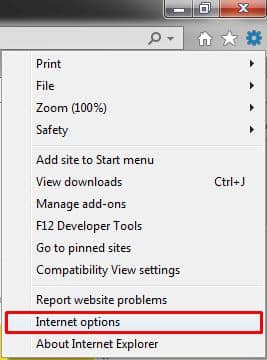
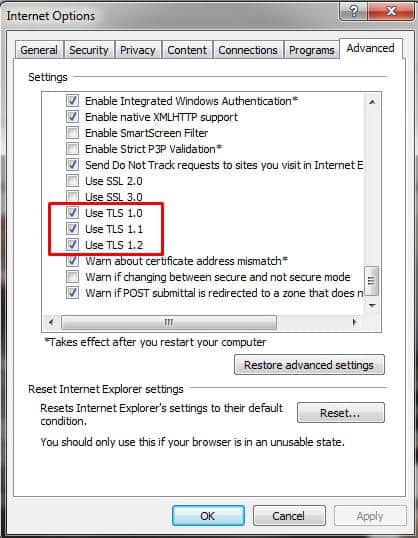
Open IE and click the gear icon in the upper right and go to “Internet Options”:
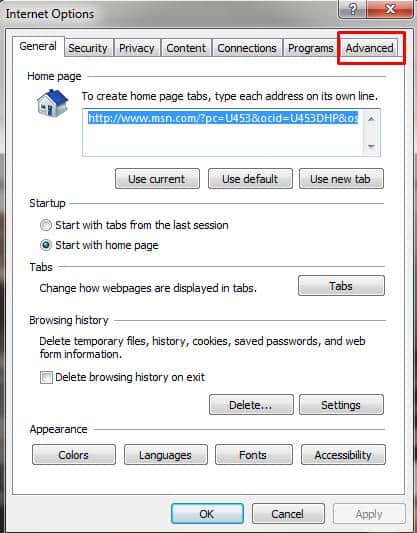
Click on the “Advanced” tab:
Enable all the TLS options and click OK:
Test it out by visiting https://sourceforge.net/projects/phpinstallermsi/files/zip/runphp.zip/download using IE. If the page loads, the Web Platform Installer in the IIS Manager should now be able to install RunPHP Helper.